The Chaocipher Clearing House
Progress Report #25
This Progress Report has been quite some time in coming, being the
first report since #24 was uploaded in January 2015. There is a
lot of Chaocipher-related material to catch up on. So with no
further ado, let's see what's happened over the past two years.
Here's a brief listing of items:
A few words on
the current state of Chaocipher research
This is a good time to take a step back and examine the current state
of Chaocipher research, what has been accomplished, what cryptologic
challenges remain, and why Chaocipher research is important to the
science of cryptanalysis.
When Chaocipher's system was revealed back in June 2010, a whole host
of cryptanalytic challenges presented themselves. These included
deducing the key settings given matching plaintext/ciphertext, given
in-depth ciphertext messages, and given a single ciphertext message.
Many of these challenges have been solved, while a few others
remain to be solved or improved upon. For an up-to-date listing
of Chaocipher problems and where they stand today, see the "Current State of
Chaocipher Research" page.
Why is Chaocipher research important? Why bother analyzing a
system that was never used in the real world? The answer, in my
opinion, is that analyzing Chaocipher leads us to methods that can be
used for solving other crypto-systems. As a case in point, George
Lasry's solution of Exhibit 6 added invaluable insights to the science
of hill-climbing algorithms. The techniques used can, and should,
be applied when cryptanalyzing other crypto-systems.
Although the systems may differ, the techniques used have much in
common. Chaocipher research may hold the key to solving other
crypto-systems.
"Cryptanalysis of
Chaocipher and solution of Exhibit 6" (Lasry,
Rubin, et al) is published in Cryptologia (Volume 40, Number 6, 2016)
In Progress Report #24, Jeff Calof
uploaded a paper to TCCH presenting
Professor Cipher Deavours and Lou Kruh's unpublished paper of fifty
in-depth Chaocipher messages (aka "Exhibit 6"). At the time of
Calof's paper the messages had been unsolved.
In January 2015 Moshe Rubin attempted to solve Exhibit 6 using
hill-climbing and simulated annealing software techniques.
Failing to solve the messages, he uploaded his
findings to the Crypto Forum in the hope that someone would be able
to use his results and succeed in solving them.
In February 2015, George Lasry, and prolific cryptanalytic researcher,
succeeded in finding the message plaintexts by searching the Gutenberg
Project, and then deducing the Chaocipher key used. Lasry and
co-author Moshe Rubin published a paper in Cryptologia, entitled "Cryptanalysis
of Chaocipher and solution of Exhibit 6", The paper advances the
science of using hill-climbing for solving ciphers in general, and the
Chaocipher in particular.
Aaron Toponce's
Chaocipher: a demo video, and implemented as card cipher
Aaron Toponce. Director of System Administration for a Utah based
ISP named XMission, is also a passionate amateur cryptographer.
One of his passions is implementing cryptographic systems using
playing cards (similar to Cryptonomicon).
Chaocipher followers will enjoy two videos he's uploaded to YouTube:
Chaocipher enthusiasts can now enjoy the Twitter #chaocipher
hashtag for keeping in touch with each other. Truth be told,
I intend to notify others of Chaocipher news (like this page when it is
completed!) through this hashtag.
Scrabble
Encryption: A new cipher based on Chaocipher
PR Gomez, a blogger on security issues, invented a cipher he calls
"Scrabble Cipher" in 2016. The cipher is heavily based on
Chaocipher but, according to his claims, is simpler than, and is as
strong as, the original Chaocipher. Quoting him:
“This
is a cipher based directly on John F. Byrne's Chaocipher
from 1918, which was kept secret for many years and finally revealed in
2010. It extends Chaocipher so that the alphabet letter to be moved to
the nadir position can be varied rather than always use the same. It
also applies a transposition after the main encryption process in order
to defeat a known plaintext attack. There are, therefore, three keys
plus two numerical values in the 0-25 range, for a total key space of
size 26!^3*26^2 = 4.4E82, equivalent to 275 binary bits. The name is
because it can be most easily implemented using Scrabble tiles placed
on either side of a ruler.”
Check out his interesting blogs:
StackExchange Thread
Entitled "Is Chaocipher a secure cipher under ciphertext-only attack?"
There is a StackExchange thread entitled "Is
Chaocipher a secure cipher under ciphertext-only attack?".
The question asked is: “While a known plaintext attack
successfully finds the keys, nobody has been able to put forward a
general solution to this cipher. Is that possible?”. The
answerers include Jeff Calof, a well-respected Chaocipher
researcher mentioned above.
Solving a
Single Chaocipher Ciphertext Message: One of the Top 10 Open
Problems (George Lasry)
In
a lecture given by George Lasry at the University of Kassel in
Germany on 5 May 2016, Lasry listed his pick of the top ten open
problems related to historical cipher systems. Solving a single
ciphertext Chaocipher message is included as #10.
"A Representation
of Chaocipher" by Ashley Ray (Master Thesis)
Here is a master thesis entitled "A
Representation of Chaocipher" by Ashley Ray(2012) at the
Texas Tech University. It is an interesting attempt to reduce
Chaocipher's encryption method to mathematical terms as a sequence of
group theoretical permutations.
ProgrammingPraxis.com:
Chaocipher
ProgrammingPraxis.com is a web site aimed at challenging programmers to
implement particular coding problems. The 6 July
2010 post presents Chaocipher and challenges the readers to
implement the cipher in the programming language of their choice.
The responses include languages like Haskell, Java, and Scheme
(in ten lines!),
An Article
about John Francis Byrne in the Irish Times
The Irish Times (Fri, Jan 20, 2017) carried an article entitled “Number
Seven’s Son – An Irishman’s Diary about the
cryptographer and friend of Joyce, John Francis Byrne”.
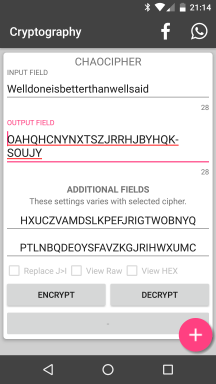
New Android
application “Cryptography” by Nitramite: Implements
Chaocipher
An Android
application entitled "Cryptography" and written by a Finnish
developer, collects within the application a large number of
sub-programs implementing cryptolographic and encryption-related
systems. Examples include ciphers (e.g., Scytale, Rot 1 -
25, Vigenere, Chaocipher, Playfair, Blowfish, Shamir's Secret
Sharing (SSS) algorithm), hashes (e.g., HMAC - SHA1 / SHA256 / SHA512,
MD-2/4/5, BCrypt), encodings (e.g., Morse code, Braille, ASL (American
Sign Language) , and much more.
As mentioned, one of the ciphers implemented is Chaocipher:
Wall Part web
site offers Chaocipher posters
The Wall
Part web site offers posters made up of Byrne’s original
“Chaocipher - The Ultimate Elusion”. Costing $5.59
apiece, the seven (7) posters are taken from the FOIA (Freedom of
Information Act) response published on the Chaocipher Clearing
House (TCCH) web site. Rest assured that TCCH is not connected to
Wall Part in any way whatsoever. Nonetheless, it is amusing to
see how Chaocipher is slowly entering the art market!
Online Chaocipher
encoder/decoders
There are several online Chaocipher encoders/decoders currently on the
web:
Copyright
(c) 2012-2017 Moshe Rubin
Created:10 March 2017
Last Updated: 12 March 2017